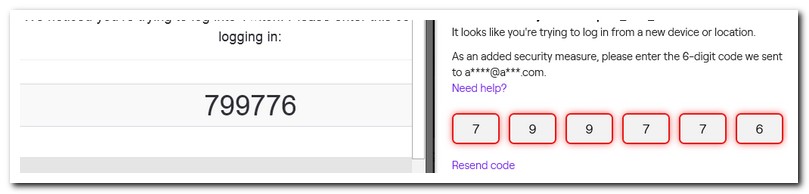
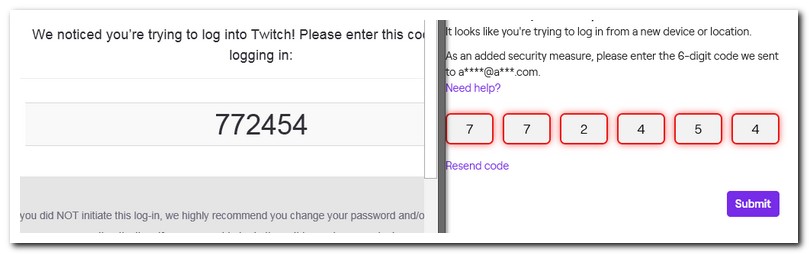
Today, my Twitch login process was one of the most ridiculous web interactions ever! As usual, Twitch sees every new browser session (cookies cleaned, no memory of the previous visited sites) as a “new device” and forces the user to provide a 6-digit code, to complement the user-password challenge. Unfortunately, those 6-digits came via email, and sloooowly, with a latency of minutes between the code request and the arrival of the corresponding email message. Maybe due to this latency, every time I entered the correct code, Twitch reacted as if I was writing the wrong number. Very frustrating.
At some stage, I finally succeeded and took the opportunity to change my Twitch security settings:
https://www.twitch.tv/settings/security
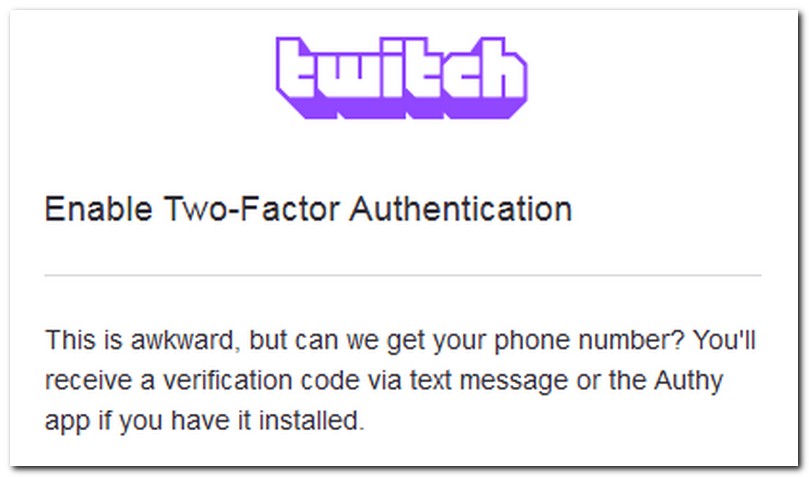
I decided to enable two-factor authentication (2FA), which means a second authentication challenge, after the user-password. First, I provided a phone-number, which indeed got associated with the account, but future logins will require not a SMS sent to the phone number, but a code generated by the “Authy” app, Twillio’s (twillio.com) equivalent to “Google Authenticator”.
When I first started using 2FA, SMS seemed the best option: I controlled the number, it required no extra app, so it was simpler, and that was – and is – something of great importance!
Unfortunately, as many are bound to find, sooner rather than later, SMS is now considerably insecure and more prone to failure than using time-sensitive security apps. The top reason SMS has failed me in the past, was phone-network operator restrictions, temporary phone-network traffic issues, and/or other reasons strictly under the phone-network operator control: there were situations when I needed a SMS in 30 seconds, and it would never arrive that promptly. That was the day when I quit SMS for app-based 2FA. The data comes from an operator agnostic network – the Internet.
Nowadays, SMS should be a second choice, relatively to Authy and equivalents, not only because of not depending on one specific phone-operator network, but also because the system is more vulnerable, with increasingly more documented SIM-card hijacking events.

Technical Details
- ./ups/2020-07/01/ARTURMARQUES_DOT_COM_WP_AMAM/twitch_02_code_correct_but_not_accepted_02_768.jpg
- attachment_id : 1053
- date_created_gmt : 2020-07-01 19:04:18
- parent : 0
- link : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_02_code_correct_but_not_accepted_02_768.jpg
- title : twitch_02_code_correct_but_not_accepted_02_768.jpg
- caption :
- description :
- metadata :
- width : 809
- height : 254
- file : 2020/07/twitch_02_code_correct_but_not_accepted_02_768.jpg
- sizes :
- medium :
- file : twitch_02_code_correct_but_not_accepted_02_768-300×94.jpg
- width : 300
- height : 94
- mime-type : image/jpeg
- thumbnail :
- file : twitch_02_code_correct_but_not_accepted_02_768-150×150.jpg
- width : 150
- height : 150
- mime-type : image/jpeg
- medium_large :
- file : twitch_02_code_correct_but_not_accepted_02_768-768×241.jpg
- width : 768
- height : 241
- mime-type : image/jpeg
- post-thumbnail :
- file : twitch_02_code_correct_but_not_accepted_02_768-672×254.jpg
- width : 672
- height : 254
- mime-type : image/jpeg
- medium :
- image_meta :
- aperture : 0
- credit :
- camera :
- caption :
- created_timestamp : 0
- copyright :
- focal_length : 0
- iso : 0
- shutter_speed : 0
- title :
- orientation : 0
- keywords :
- type : image/jpeg
- thumbnail : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_02_code_correct_but_not_accepted_02_768-150×150.jpg
- id : 1053
- file : twitch_02_code_correct_but_not_accepted_02_768.jpg
- url : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_02_code_correct_but_not_accepted_02_768.jpg
- ./ups/2020-07/01/ARTURMARQUES_DOT_COM_WP_AMAM/twitch_03_code_correct_and_accepted_768.jpg
- attachment_id : 1054
- date_created_gmt : 2020-07-01 19:04:19
- parent : 0
- link : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_03_code_correct_and_accepted_768.jpg
- title : twitch_03_code_correct_and_accepted_768.jpg
- caption :
- description :
- metadata :
- width : 809
- height : 310
- file : 2020/07/twitch_03_code_correct_and_accepted_768.jpg
- sizes :
- medium :
- file : twitch_03_code_correct_and_accepted_768-300×115.jpg
- width : 300
- height : 115
- mime-type : image/jpeg
- thumbnail :
- file : twitch_03_code_correct_and_accepted_768-150×150.jpg
- width : 150
- height : 150
- mime-type : image/jpeg
- medium_large :
- file : twitch_03_code_correct_and_accepted_768-768×294.jpg
- width : 768
- height : 294
- mime-type : image/jpeg
- post-thumbnail :
- file : twitch_03_code_correct_and_accepted_768-672×310.jpg
- width : 672
- height : 310
- mime-type : image/jpeg
- medium :
- image_meta :
- aperture : 0
- credit :
- camera :
- caption :
- created_timestamp : 0
- copyright :
- focal_length : 0
- iso : 0
- shutter_speed : 0
- title :
- orientation : 0
- keywords :
- type : image/jpeg
- thumbnail : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_03_code_correct_and_accepted_768-150×150.jpg
- id : 1054
- file : twitch_03_code_correct_and_accepted_768.jpg
- url : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_03_code_correct_and_accepted_768.jpg
- ./ups/2020-07/01/ARTURMARQUES_DOT_COM_WP_AMAM/twitch_04_2fa_about_to_be_enabled_768.jpg
- attachment_id : 1055
- date_created_gmt : 2020-07-01 19:04:22
- parent : 0
- link : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_04_2fa_about_to_be_enabled_768.jpg
- title : twitch_04_2fa_about_to_be_enabled_768.jpg
- caption :
- description :
- metadata :
- width : 809
- height : 477
- file : 2020/07/twitch_04_2fa_about_to_be_enabled_768.jpg
- sizes :
- medium :
- file : twitch_04_2fa_about_to_be_enabled_768-300×177.jpg
- width : 300
- height : 177
- mime-type : image/jpeg
- thumbnail :
- file : twitch_04_2fa_about_to_be_enabled_768-150×150.jpg
- width : 150
- height : 150
- mime-type : image/jpeg
- medium_large :
- file : twitch_04_2fa_about_to_be_enabled_768-768×453.jpg
- width : 768
- height : 453
- mime-type : image/jpeg
- post-thumbnail :
- file : twitch_04_2fa_about_to_be_enabled_768-672×372.jpg
- width : 672
- height : 372
- mime-type : image/jpeg
- medium :
- image_meta :
- aperture : 0
- credit :
- camera :
- caption :
- created_timestamp : 0
- copyright :
- focal_length : 0
- iso : 0
- shutter_speed : 0
- title :
- orientation : 0
- keywords :
- type : image/jpeg
- thumbnail : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_04_2fa_about_to_be_enabled_768-150×150.jpg
- id : 1055
- file : twitch_04_2fa_about_to_be_enabled_768.jpg
- url : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_04_2fa_about_to_be_enabled_768.jpg
- ./ups/2020-07/01/ARTURMARQUES_DOT_COM_WP_AMAM/twitch_05_2fa_on_768.jpg
- attachment_id : 1056
- date_created_gmt : 2020-07-01 19:04:23
- parent : 0
- link : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_05_2fa_on_768.jpg
- title : twitch_05_2fa_on_768.jpg
- caption :
- description :
- metadata :
- width : 809
- height : 779
- file : 2020/07/twitch_05_2fa_on_768.jpg
- sizes :
- medium :
- file : twitch_05_2fa_on_768-300×289.jpg
- width : 300
- height : 289
- mime-type : image/jpeg
- thumbnail :
- file : twitch_05_2fa_on_768-150×150.jpg
- width : 150
- height : 150
- mime-type : image/jpeg
- medium_large :
- file : twitch_05_2fa_on_768-768×740.jpg
- width : 768
- height : 740
- mime-type : image/jpeg
- post-thumbnail :
- file : twitch_05_2fa_on_768-672×372.jpg
- width : 672
- height : 372
- mime-type : image/jpeg
- twentyfourteen-full-width :
- file : twitch_05_2fa_on_768-809×576.jpg
- width : 809
- height : 576
- mime-type : image/jpeg
- medium :
- image_meta :
- aperture : 0
- credit :
- camera :
- caption :
- created_timestamp : 0
- copyright :
- focal_length : 0
- iso : 0
- shutter_speed : 0
- title :
- orientation : 0
- keywords :
- type : image/jpeg
- thumbnail : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_05_2fa_on_768-150×150.jpg
- id : 1056
- file : twitch_05_2fa_on_768.jpg
- url : https://arturmarques.com/wp/wp-content/uploads/2020/07/twitch_05_2fa_on_768.jpg